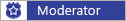
My boot logs show chinese ip, anyway to prevent this?
I am using lastest ayufan's image
![[Image: X7UEpXC.png]](https://i.imgur.com/X7UEpXC.png)
![[Image: GcmM8jX.png]](https://i.imgur.com/GcmM8jX.png)
I am using lastest ayufan's image
Code:
root@rock64:~# uname -a
Linux rock64 4.4.126-rockchip-ayufan-239 #1 SMP Sun May 27 18:38:24 UTC 2018 aarch64 GNU/Linux
root@rock64:~#![[Image: X7UEpXC.png]](https://i.imgur.com/X7UEpXC.png)
![[Image: GcmM8jX.png]](https://i.imgur.com/GcmM8jX.png)